Zero-Trust
Network Security
Trust Nothing. Secure Everything.
As organizations adopt remote work-from-home policies, bring-your-own-mobile-devices and cloud-based applications, perimeter defenses are no longer enough. Zero-trust network access assumes no user or device is trustworthy to ensure users only have access to the specific data and applications they need. Our Cyber-on-Call® Division implements zero-trust network security to prevent malicious actors from using compromised credentials to access sensitive network data.
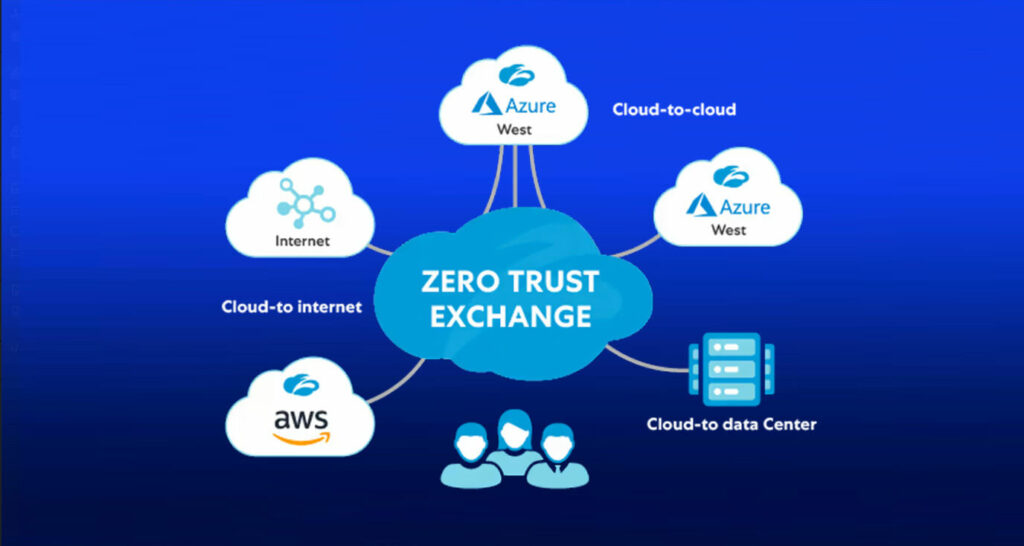
Isolate Networks
Isolate network, data and IT resources to prevent unauthorized access from remote devices, on-premise and in the cloud.
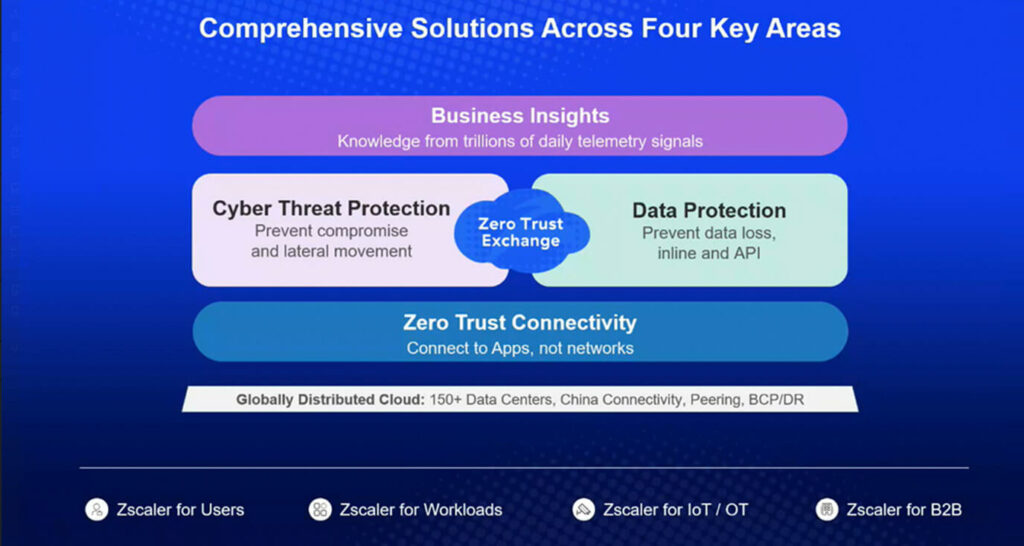
Restrict Access
Enforce granular, least-privilege user access controls across distributed IT networks and multi-cloud environments.
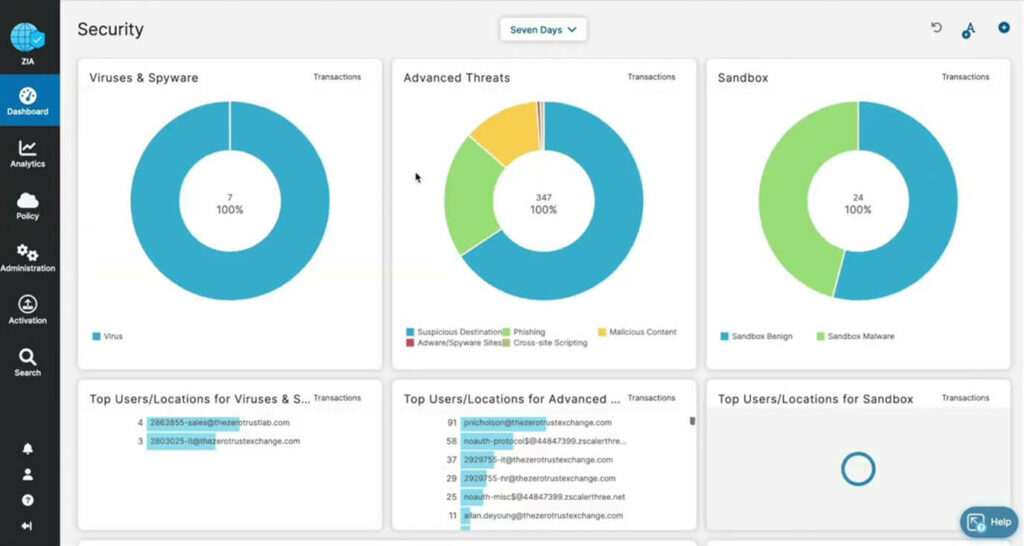
Enforce Policies
Accurately identify & authenticate every user and device access request to prevent data breaches and ransomware.